× close
Credit: Duke University
A black sedan drives silently down a quiet suburban road, the driver quietly humming Christmas carols, and the car's autopilot takes charge. Suddenly, a flashing red light and a beeping sound pulled the driver from his peaceful respite. When you look at the dashboard screen, you can see the outline of a car coming towards you at high speed, about to hit you head-on, but with your headlights you can't see anything in front of you through the windshield.
Despite the discomfort, the car's autopilot took control and veered into a ditch. The driver looked around in exasperation, but once the approaching danger disappeared from the screen, he saw no other vehicles. Soon, the real threat appears. A group of hijackers trots toward a stuck vehicle.
This scene seems destined to become a common plot point in Hollywood movies for decades to come. However, the complexity of modern vehicle detection systems remains in the realm of science fiction. At least for now.
Duke University engineers led by Miroslav Pajic, Dickinson associate professor of electrical and computer engineering, and Tingjun Chen, assistant professor of electrical and computer engineering, demonstrate a system they call MadRadar for fooling automotive radar sensors. did. You begin to believe that almost anything is possible.
This technology can hide the approach of an existing car, create a phantom car where none exists, or even fool radar into thinking a real car has quickly deviated from its actual course. . And they can accomplish this feat in the blink of an eye, without any prior knowledge of the victim's radar's specific settings, making it the most vexing threat to radar security yet.
Researchers say MadRadar shows that manufacturers need to start taking immediate steps to better protect their products.
This research is currently arXiv The preprint server will be unveiled at the 2024 Network and Distributed Systems Security Symposium, February 26-March 1 in San Diego, California.
“You can make a fake car appear out of nowhere or make a real car disappear in a real-world experiment without knowing much about the target car's radar system,” Pasik said. “We're not building these systems to hurt anyone. We're building these systems to demonstrate the problems that exist in current radar systems and show that we need to fundamentally change the way they're designed.” It is.”
Modern cars with assistance and autonomous driving systems typically use radar to detect moving vehicles in front of and around the vehicle. It also enhances vision and laser-based systems to help detect vehicles moving in front of or behind the car.
Today, so many different vehicles use radar on a typical highway that it is unlikely that two vehicles will have exactly the same operating parameters, even if they are the same make and model. . For example, they may use slightly different operating frequencies or take measurements at slightly different intervals. For this reason, previous demonstrations of radar spoofing systems required knowing the specific parameters being used.
“Think of it like trying to stop someone from listening to the radio,” Pajic explained. “Before you can block a signal or hijack a signal with your own broadcast, you first need to know which station the other person is listening to.”
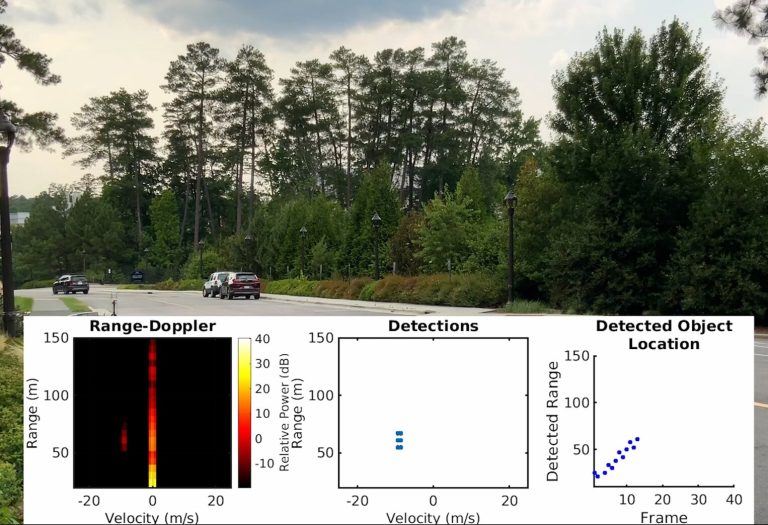
In the MadRadar demonstration, the Duke University team showed off the capabilities of a radar spoofing system they developed that can accurately detect a vehicle's radar parameters in less than a quarter of a second. Once they are discovered, the system can transmit its own radar signal to fool the target's radar.
In one demonstration, MadRadar sends a signal to a target car to make it recognize another car that isn't actually there. This involves changing the characteristics of the signal based on time and speed to mimic what real contact would be like.
A second, more complex example is to trick the target's radar into thinking the opposite is true: there are no passing cars when in fact there are. It accomplishes this by carefully adding a masking signal around the vehicle's actual location, creating a kind of bright spot that confuses radar systems.
“You have to be careful when adding signals to a radar system, because if you just send a signal across the field of view, you'll quickly know something is wrong,” says Dr. David Hunt. says. A student working in Pazic's laboratory.
In a third type of attack, researchers combine the two approaches to make it appear as if an existing car suddenly changed course. The researchers recommend that automakers randomize the operating parameters of their radar systems over time and add safeguards to their processing algorithms to detect similar attacks.
“Imagine if your adaptive cruise control, which uses radar, tricks you into thinking the car in front of you is speeding up and causes your car to speed up too, when in fact your speed hasn’t changed at all. ''Pazic said. “If this was done at night, by the time your car camera would notice it, you'd be in trouble.”
The researchers stress that both of these attack demonstrations were conducted on real-world radar systems mounted on real cars traveling at road speeds. This is an impressive feat, considering that if a spoof's radar signal is off the mark by just one microsecond, the fake data point will be misplaced by as long as a football field.
“These lessons go far beyond automotive radar systems,” Pajic said. “If you want to build a drone that can explore dark environments for search and rescue or reconnaissance operations without costing a few thousand dollars, radar is the way to go.”
For more information:
David Hunt et al., MadRadar: A Black-Box Physical Layer Attack Framework on Millimeter-Wave Automotive FMCW Radar, arXiv (2023). DOI: 10.48550/arxiv.2311.16024